Platform’s Architecture and Features
Main Concepts
- Anything in the infrastructure that is “monitorable” / “scriptable” / “API-able” may be handled by the platform as an Event
- Infrastructural events are managed using a multiple workflow concept. Each defined Event will run in its own workflow
Platform Components
Web Platform: the web interface to manage your organization’s infrastructures.
Analysis Engine: instance which analyzes events and matches rule conditions to execute actions. May deploy multiple instances for balancing load.
Data Collection Nodes: collect events from infrastructural nodes and transports them to the web platform. You may deploy multiple instances for balancing load.
Cross O.S. Agent: the software agent which may run on Linux/Windows instances, handles the node’s heartbeat for the platform. Note: the platform may also work without agents, by using other methods to intercept and send events to the web platform. The agent gives more control and interaction with the instance.
Security features
- Platform and its APIs use HTTPS
- Events sent by Data Collector Nodes use TLS encrypted transport channel
- Commands sent for execution from platform to nodes are AES encrypted
- Frontend API calls use a OTP token for each call
Web Platform Functionalities
- Define Infrastructural Events (On-prem, Hybrid, Cloud)
- Choose the source & method to intercept the Event
- Log file / text file evaluation (tail mode)
- Run command (response evaluation)
- Call API endpoint (response evaluation)
- Call HTTP URL (response evaluation)
- Windows Event (filter per event ID)
- Semaphore file check (check file exists)
- System parameter (evaluate value)
- Read email (parse subject/text IMAP mode)
- Choose the source & method to intercept the Event
The images below show the definition of an Event aka Indicator. We may want to define an event only for a certain set of nodes. An event may originate from a source based on a matching condition, for e.g.: from a log file on an instance, based on the output of a command run on an instance, based on an API or HTTP response, an email content, a system parameter, the existance of a semaphore file of a windows event.
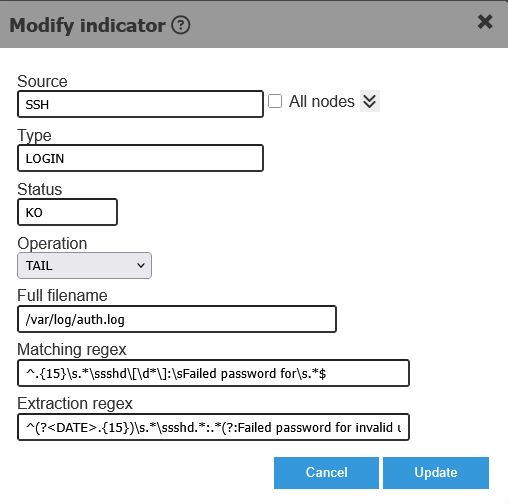
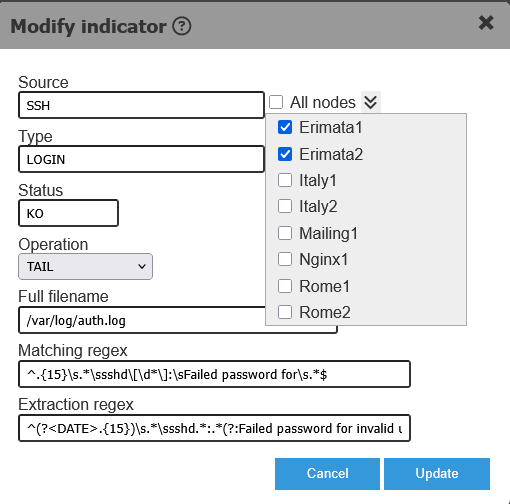
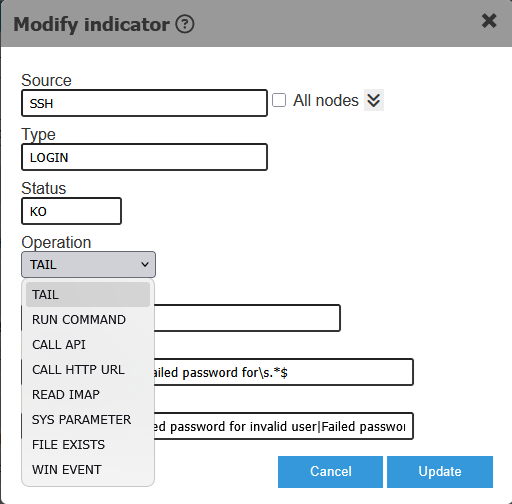
- Define Conditions (Rules) related to the event which determine the execution of an action
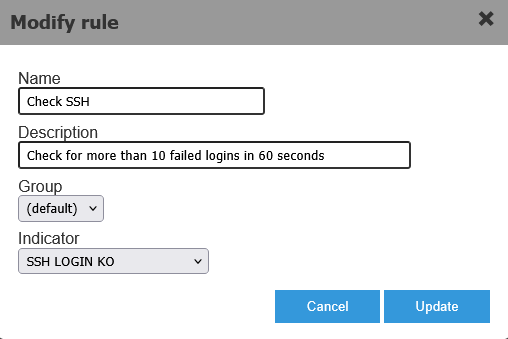
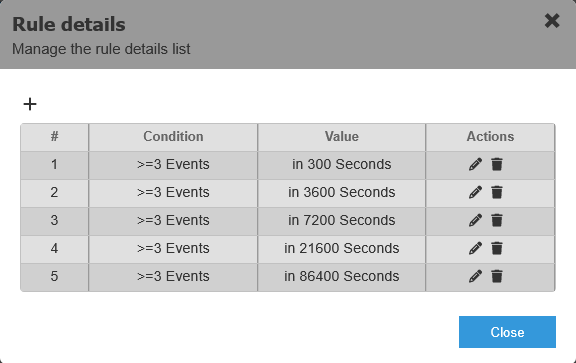
The following images show a condition definition for a specific event (SSH LOGIN KO). We are interested in that event only when it satisfies the rule details.
- Define Actions to be executed when an Event occurs
- Actions may be implemented as high level commands which will execute O.S. specific commands
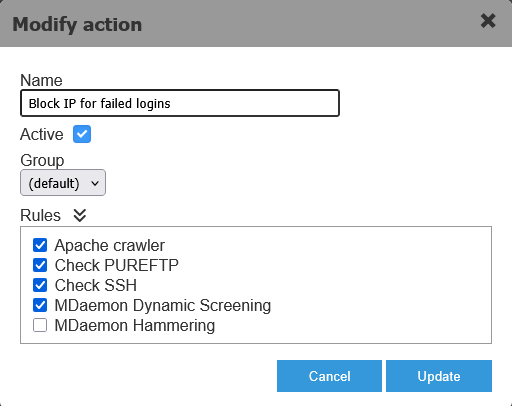
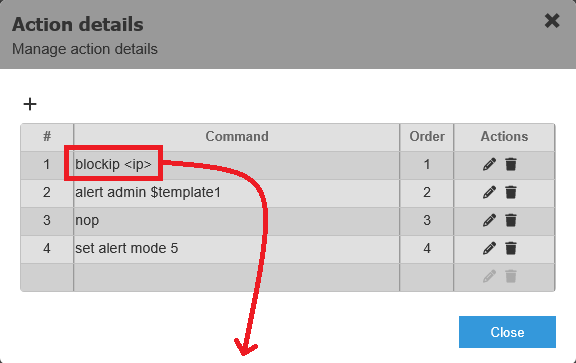
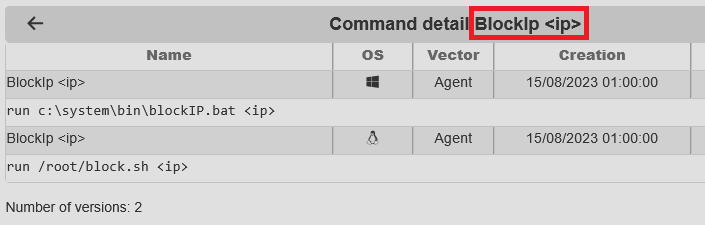
The images below show the definition of an Action (associated to Rule conditions); the Action detail which will run 4 commands on the nodes; and an excerpt of the BlockIp platform command which will automatically translate to a Windows script and a Linux script:
- View and search Events
- Manage Infrastructural Nodes
- Define an infrastructural node
- Organize nodes in groups
- Send commands directly to a node or to a group of nodes via CLI (requires installed agent)
- Node heartbeat is sent automatically to platform (requires installed agent)
- Send commands directly to a node or to a group of nodes via CLI (requires installed agent)

- Manage IP address knowledge base
- Event which are IP connected populate the IP Dossier database, containing all info known for that IP including the event history

- View and search Operations list
- All actions executed by the platform based on the Rule-Action definition are stored
- Access graphical analytics dashboards
Coming Up in V2
- Mobile App: first implementation will be connected to the alerting system
- AI modules
- Users may manage Workflows with a graphical UI
- Standard Compliance: map Events and Actions to international standards (ISO/IEC, UAE ADISS, UAE IAR, etc)
- Define Honeypot Nodes: to catch attack patterns with fake services (SSH, FTP, etc)
