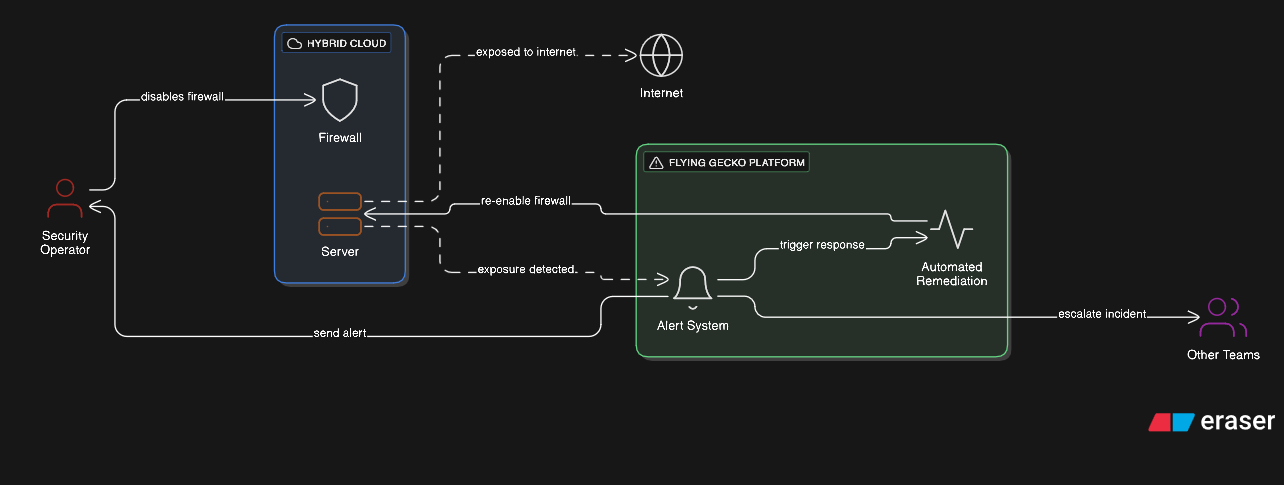
Description: a typical attack case which may occur against many different types of protocols (SSH, HTTP, FTP, etc) consisting on unwanted or not authorized accesses logged by the O.S. or by a service or an application. The common factor in this attack is the frequency and the status of the requests coming from the attacker. The goal is to block the attacker access to the entire infrastructure.
Scenario: during normal activity an excessively high rate of requests, or of non authorized access, are measured on an infrastructural node. Or the unwanted accesses may be executed at a slower, but constant, rate (for e.g. 200 non authorized attempts to login to an FTP or SSH service, over a 3 days time frame).
Solution: model an Event on the platform, one for each protocol (or application) to protect, by creating an indicator to represent the incoming non authorized access. This is done by defining the pattern we want to intercept in the log files. When the rate exceeds the defined threshold(s), the platform will activate the remediation action by blocking access to the attacker.